Study Notes

Overview
Ethical issues in computer science (WJEC 8.1) explore the moral dilemmas created by digital technology. This topic isn't just about rules; it's about evaluating the impact of technology on individuals and society. You'll be expected to understand the tension between technological progress and fundamental rights concerning privacy, data security, and the ownership of digital creations (intellectual property). In the exam, this is a prime topic for extended writing questions (6-9 marks) where you must present a balanced argument, considering multiple viewpoints. Mastering this area shows you can think critically like a computer scientist, connecting technical concepts to their real-world consequences.
Key Concepts
Concept 1: Privacy vs. Security
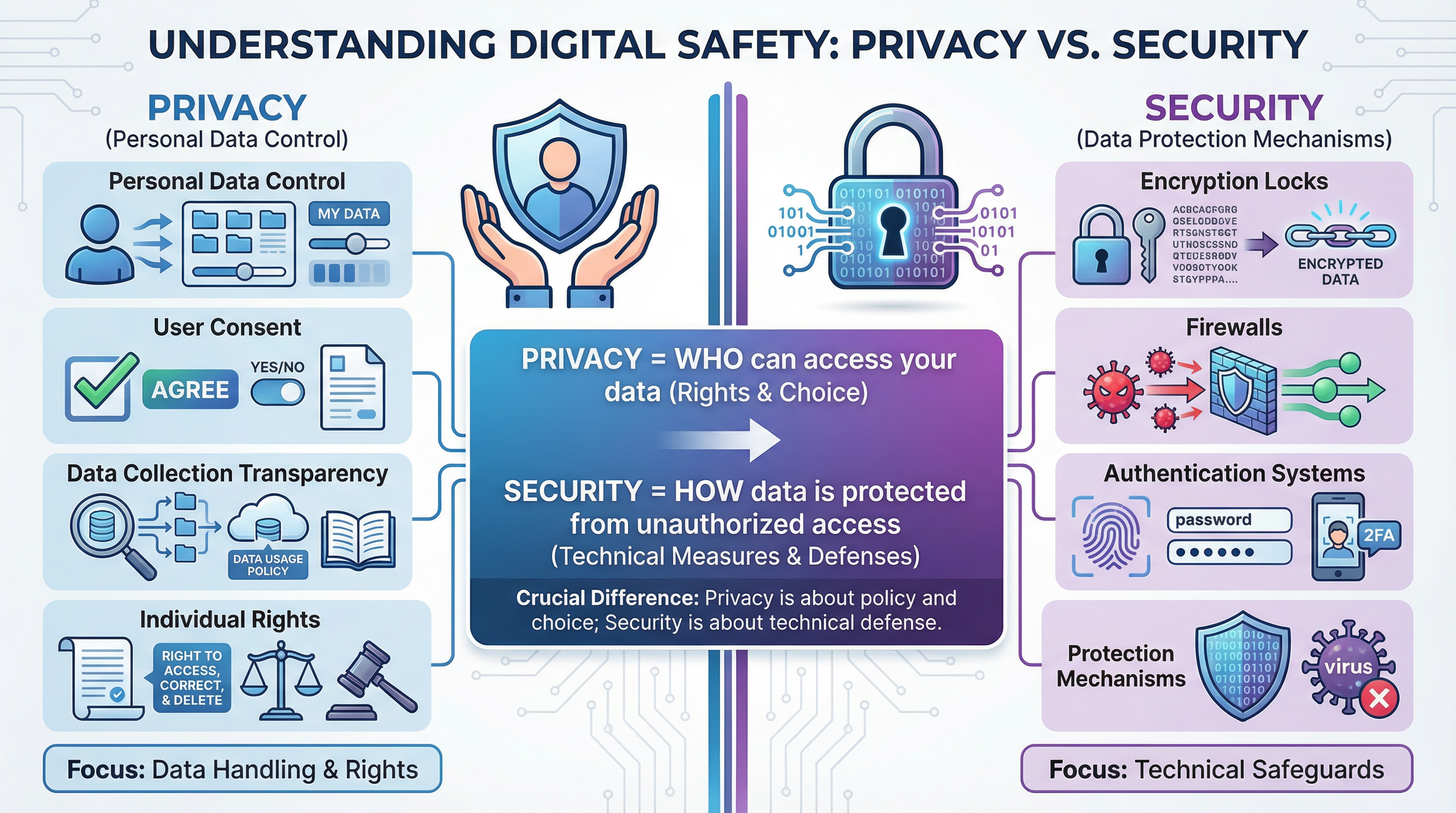
This is the most fundamental distinction and a common source of confusion for candidates. Getting this right is an easy mark.
Privacy is the right of an individual to control their personal data. It answers the question: WHO should have access to my information and WHAT can they do with it? It involves principles of consent (did you agree to data collection?), transparency (does the company tell you what it's collecting?), and purpose (is the data being used for the reason it was collected?).
Security is the mechanism used to protect data from unauthorized access. It answers the question: HOW is the data kept safe? This includes all the technical measures: encryption, firewalls, access controls (passwords, biometrics), and anti-malware software. Security is the toolbox that helps enforce privacy policies.
Crucial Analogy: Think of your house. Privacy is your decision about who you invite inside (friends, family, the postman). Security is the lock on your front door, the alarm system, and the strong windows that prevent uninvited people from getting in. You can have a great lock (security) but still have your privacy violated if you invite someone untrustworthy inside.
Concept 2: Intellectual Property (IP)
Intellectual Property refers to creations of the mind. In computing, this is vital as most of the value is in the software, algorithms, and digital content, not physical products. Protecting IP encourages innovation by allowing creators to benefit financially from their work.
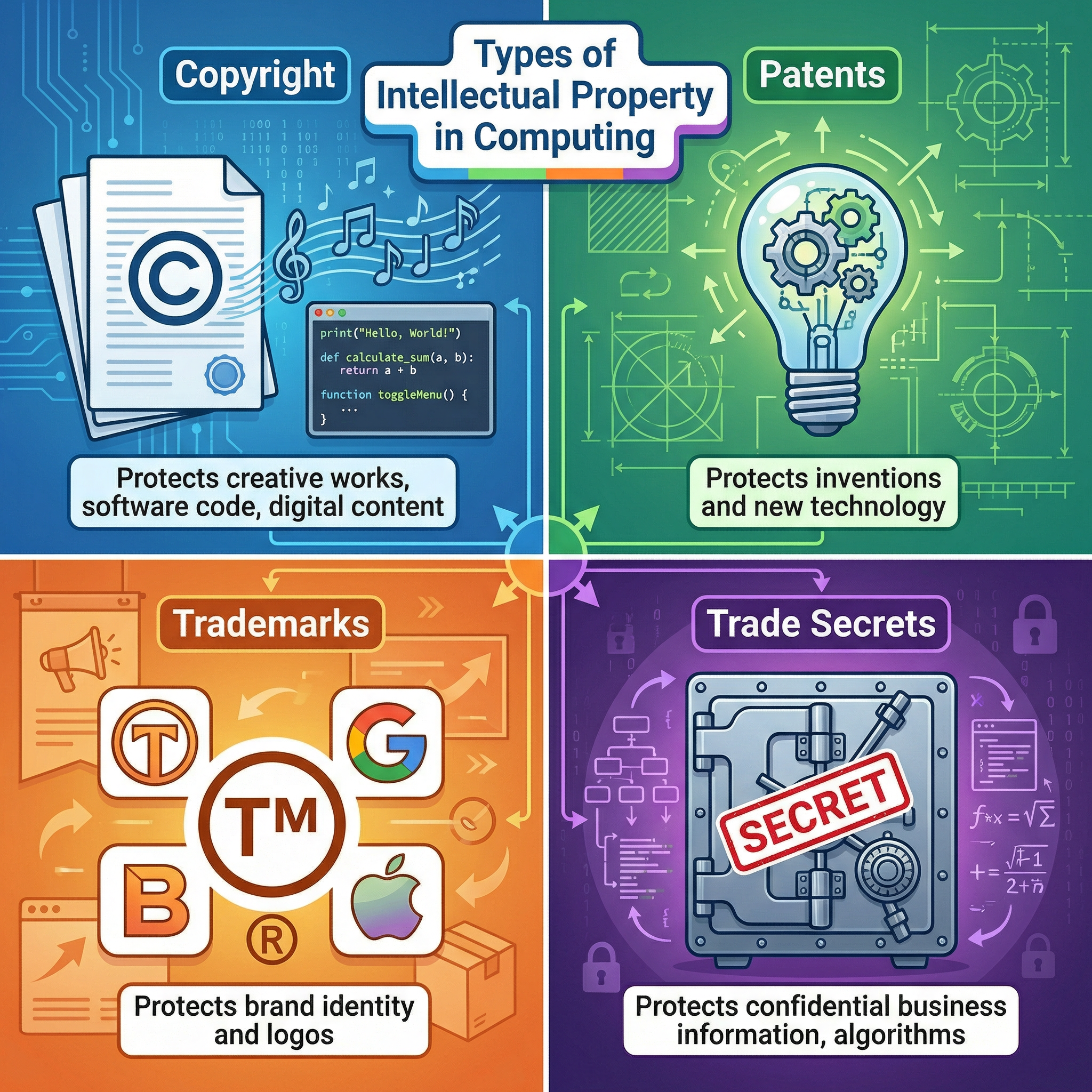
There are four main types you need to know:
- Copyright: Automatically protects original creative works, such as software source code, music, photos, and written text. It makes it illegal to copy, modify, or distribute the work without the creator's permission. The symbol is ©.
- Patents: Protects new inventions, processes, or technologies. In computing, a company might patent a new type of algorithm or a hardware innovation. This provides exclusive rights for a set period (usually 20 years). It is much harder and more expensive to get than copyright.
- Trademarks: Protects brand identity, such as logos, names, and slogans, that distinguish one company's products from another. The symbols are ™ and ®.
- Trade Secrets: Confidential business information that gives a company a competitive edge. Examples include the source code for Google's search algorithm or the specific formula for a chemical process. It is protected by keeping it secret, often through non-disclosure agreements (NDAs).
Concept 3: The Stakeholder Conflict
Ethical issues are rarely simple because different groups of people (stakeholders) have conflicting interests. For any ethical scenario, you must consider who is affected and what their perspective is. This is essential for high-mark answers.
Example Scenario: A social media company introduces a new feature that uses AI to scan users' private messages to suggest products to buy.
- End Users: Their privacy is reduced. They may feel spied on and that their personal conversations are being exploited for commercial gain.
- The Company (Social Media Platform): They can generate more revenue from highly targeted advertising. This makes their business more profitable and allows them to offer a 'free' service.
- Advertisers: They get a more effective way to reach potential customers, increasing their sales and return on investment.
- Government/Regulators: They are concerned with protecting citizens' rights and ensuring the company complies with data protection laws. They may investigate and fine the company if it breaks the rules.
Being able to identify these stakeholders and their competing interests is a hallmark of a top-level answer.
Practical Applications
- Digital Rights Management (DRM): Technology used by content owners (e.g., movie studios, game developers) to control how you can use the content you've purchased. For example, it might prevent you from copying a DVD, sharing an ebook with a friend, or playing a game offline. This is a direct application of enforcing copyright.
- Open Source Software: Software where the source code is made freely available for anyone to view, modify, and redistribute. Examples include the Linux operating system and the Firefox web browser. This contrasts with proprietary software (like Microsoft Windows or Adobe Photoshop) where the source code is a trade secret.
- Privacy Policies: The legal documents you agree to when you sign up for a service. They outline what data is collected (transparency) and how it will be used (purpose). While often ignored, they are a key part of the privacy framework.
